What Is Proctoring?
The Ultimate Guide

This is your definitive guide to all things proctoring in 2025.
In this complete guide, you’ll learn about:
- The different types of proctoring
- The security threats proctors can and can’t address
- The effectiveness of proctoring measures
- How to choose your proctoring vendor
- And lots more
So if you’re curious about proctoring, whether it’s right for your program, or the security benefits it offers, then this is the guide for you.
Let’s get started!
Contents
What Is Proctoring?
For centuries, people have relied on proctoring as their main exam security measure.
In fact, the earliest known use of proctors occurred more than 2,000 years ago on the Imperial Civil Service Exams in China. You can learn more about the history of proctoring in this really neat white paper, but for now, let’s focus on the fundamentals.
In this chapter, you’ll get a handle on:
- What proctoring is
- How a proctored exam works
- Why it’s important
- Its benefits
- And more
Then, in later chapters, we’ll touch on the most important question for our time: is proctoring a robust enough exam security measure on its own? We’ll also find out where proctoring needs help bolstering security and what you need to consider when choosing a proctoring vendor for your testing program.
Let’s dive right in!
What Is Proctoring?
Proctoring is the act of observing test takers while they take an exam. The exam is ideally supervised via a neutral third party, and it is often done over a webcam (online proctoring).
The role of a proctor is both:
- Administrative
- (For example, checking in test takers, administering the exam, etc.) and
- Security-focused
- (For example, helping to prevent test takers from cheating or stealing test content, ensuring that the security and integrity of the test being given remains intact, etc.)
But why is a test’s security so important?
Good question!
When we have proper exam security measures in place, the results a test produces will reflect fair and valid testing measures and test-taking practices, which are the factors that make the use of test scores trustworthy and meaningful in the first place.
Without exam security measures in place, we can’t really know if the people who are passing their exams really have the knowledge and skills they need to do so!
Examinations would be worthless if we couldn’t trust their results, and security measures are put in place to make sure that we can!
Different Methods of Proctoring
There are four different proctoring practices used today:

1. Live Proctoring (Either On-Site or Remote)
Live proctoring is when a test taker is monitored by testing or third-party staff in real time throughout the duration of the exam. This can be done in person or in remote settings, depending on the method of exam delivery.
When done remotely (oftentimes referred to as remote or online proctoring), the exam takes place live over the internet with the test taker and the proctor in separate locations. The test is usually monitored over a webcam, and sometimes screen-shared.
For online proctoring specifically, methods proctors use to protect exams may include:
- Video from capable webcams
- The option to have control over the test session
- Chat-based communication
- Automated monitoring (more on this below), and
- Unique authentication software methods
Whether on-site or online, proctors in any form of live setting must be well-versed in the cheating and test fraud threats that face exams and comfortable with confronting any issues head on when they are spotted.

2. Recorded Proctoring (Remote)
Record and review proctoring is when an examinee’s test session is recorded through both video and audio, and then later reviewed by testing or third-party staff after the exam has ended.
The review could take place anywhere from one day or even a year later (though ideally the review process is done as quickly as possible, just in case there really was cheating or test fraud that took place). We’ll touch on record and review proctoring more in depth in Chapter 6.

3. Hybrid Proctoring (Either On-Site or Remote)
Hybrid proctoring is the combination of two or more proctoring methods.
For example, automated artificial intelligence (AI) proctoring could be used with record & review proctoring.
In that case, AI proctoring would first identify instances where potential testing malfeasance(s) may have occurred, and then a human proctor could later review the flags to confirm or deny whether cheating or test fraud actually took place.

4. Automated Proctoring (On-Site or Remote)
In automated proctoring, a computer-based exam has the ability to pause or terminate the test when a potential security breach is detected. (Since computer-based exams can happen both in person and remote, this proctoring method can work either way.)
For example, Caveon Scorpion™ can identify certain types of cheating or test theft right as they are occurring. It can detect when a test taker enters certain keystrokes that are common with cheating, or when an examinee copies + pastes text, opens a new browser window, and more. It alerts exam staff as soon as it happens so they can decide what to do in real time.
(Kind of cool, right?)
While each type of proctoring has strengths and weaknesses, overall, they perform a very similar service.
Let’s look more closely at the role of proctors…
The Role of Proctors
Live proctors perform many of the same tasks, whether in person or remote.
Proctors are responsible to:
- Observe test takers while they take an exam
This is a two-part responsibility that requires proctors to:- Prevent test takers from stealing test content
- Prevent test takers from cheating
- Perform various administrative tasks that are unrelated to security
In the end, much like the exam programs they help represent, proctors are hopeful that they won’t be called on to handle any test security incidents because they are, in general, not paid very much (and sometimes they are even volunteers!).
Training for proctors is oftentimes brief, but in other instances, proctors are trained for many weeks and must take a certification exam to begin monitoring.
But no matter the training, proctors are asked to do a difficult chore: to stop test fraud as soon as they detect it.
And there’s more to it than that…
The Responsibilities of Proctors
Usually, proctors are asked to:
- Sign in test takers for the exam
- Check identification and make sure examinees are who they say they are
- Provide instructions to the test taker and read rules aloud
- Answer questions examinees may have before, after, and during the test
- Watch for cheating
- Look out for test theft
- Address problems right as they are happening
- Dismiss examinees at the end of an exam
- Serve as the professional face of your testing organization
As you can imagine, that’s a lot of tasks to juggle! Proctors really are asked to fill and complete some pretty complex roles and tasks.
However, it’s important to note that some test fraud, occurring right under their noses, is virtually impossible for proctors to see…
In all, proctoring is one method that can help curtail test fraud and improve test security.
(Though it’s not a particularly effective security method–more on this in Chapter 4. Other more enhanced methods include secure test designs, data forensics, web monitoring, and others.)

To conclude chapter 1, a proctored exam is a test that is monitored by staff or by a neutral third party in order to prevent test takers from cheating or stealing test content.
There are 4 types of proctoring that can occur, whether in person or remotely:
- Live Proctoring (either in person or remote)
- Recorded Proctoring (remote)
- Hybrid Proctoring (either in person or remote)
- Automated Proctoring (either in person or remote)
Up next in Chapter 2, we’ll talk about the benefits of proctoring and uncover the different types of cheating proctors are able to catch.
Then, in Chapters 3-7, we’ll cover proctoring’s effectiveness, its drawbacks, whether un-proctored online exams can be trusted, and more.
Onward!
The Benefits of Proctoring
In this chapter, we’ll explore the many security benefits of proctoring exams.
We’ll also cover the types of security breaches proctors can help us identify and catch.
Let’s dive in!
The Benefits of Proctoring

1. Reduced testing violations

2. Reduced security breaches

3. Better technology over time
(The technology used for online proctoring can improve with time and increase the effectiveness of proctoring. For example:
- Artificial intelligence and machine learning for monitoring candidates with facial recognition
- The automatic detection of hidden devices
- The use of data forensics and its impact of uncovering cheating and collusion
- The use of test designs that reduce overall item exposure [such as AIG or SmartItem™ technology])
Additional Benefits, Specific to Online Proctoring, Include:

1. Reduced costs associated with testing (e.g., testing fees, travel costs, parking passes, etc.)

2. Added convenience for test-takers, proctors, and instructors to take and administer tests in their homes, schools, or workplaces

3. Increased effectiveness. Research indicates that (when properly applied) online proctoring methods can be as or more effective than traditional proctoring occurring in testing centers.
What Types of Cheating & Test Theft Can Proctors Catch?
Proctors should catch:
- Cheat sheets used during the exam
- Phones or other devices that can be used as cheating aids
- Earpieces that examinees use to receive answers from a third party outside of the testing room (In-person proctors)
- Conversations among other examinees
- Other conversations with people in or near the testing space who aren’t taking the exam
- Earpieces that examinees use to receive answers from a third party outside of the testing room (In-person proctors)
- Examinees leaving the testing space
- Phones or other devices that can be used as cheating aids
- Obvious illicit materials in the exam space (textbooks, notepads, etc.)
- Copying answers from another test taker (in-person proctoring only)
With the above scenarios in mind, you can imagine the pressure is high for proctors, especially when they’re monitoring very high-stakes exams!
Test Security Threats
THAT PROCTORING UNCOVERS
Proctors should catch...
Proctors can't catch...
- Cheat sheets
- Phones or other devices
- Earpieces
- Conversations with other examinees
- Conversations with others in/near the testing space not taking the exam
- Examinees leaving the testing space
- Obvious illicit materials (textbooks, notepads, etc.)
- Copying answers from another test taker
- Pre-knowledge
- Proxy test taking
- Small hidden cameras
- Test theft
- Examinees who have hacked into the testing server to retrieve answers
- Examinees who are memorizing test questions to sell to braindump sites
In the best of circumstances, proctors can detect many security breaches.
Important to note, however, is that proctors can’t catch everything…
In fact, proctors can’t catch many of the most nefarious and effective methods of cheating or test content theft (but it’s not their fault!).
And while some forms of proctoring are suitable for high-stakes testing, others actually increase the risk of cheating!
Up next in Chapter 3, we’ll talk about the drawbacks of proctoring and cover all the types of cheating proctors aren’t quite able to catch on their own.
Here we go!
The Drawbacks of Proctoring
In Chapter 2, we explored the benefits of proctoring.
In this chapter, we’ll discuss some of the downsides of proctoring.
And you’ll also learn about the types of cheating proctors can’t catch!
Let’s get started!
Is Proctoring Alone Effective at Preventing or Catching Exam Cheating?
Simply put: No.
Many testing programs still rely a bit too heavily on proctors—particularly when proctoring is a program’s main test security strategy.
As we know, there are always individuals (even in proctoring) who are willing to cut corners without understanding or disclosing the security problems to an unwary testing program. Then, it isn’t until later when widespread cheating comes to light that the testing program actually recognizes the flaws.
Therefore…
Until testing programs understand the many possible security risks and create technology and procedures to protect the exam, proctoring will remain appropriate for only low-stakes exams when used as the sole security measure.
(And even then, most forms of cheating can elude proctors!)
The Drawbacks of Proctoring
Many Security Risks Are Associated with Proctoring.
There are three examples of security risks associated with proctoring (and some that proctoring may even introduce):
1. Proctors can view the test taker's screen during an exam
A serious security and privacy risk, proctors who have this ability could view a test taker’s screen, see the questions presented, and identify the answer provided by the test taker. This provides opportunity for both collusion with proctor / examinee and harvesting of test content to sell it on the internet.
2. Laptop cameras provide a limited head-and-shoulder-view of the examinee during testing
Many cameras don’t provide the proctor with a sufficient view of the testing environment during the exam. When this is the case, it is almost impossible to detect most attempts at cheating. Additionally, these cameras can’t spot hidden cameras or other testing contraband. Check out the picture at the end of this section and see if you can spot any hidden cameras!
3. Authentication failures can happen and privacy concerns are introduced when verifying examinees
Having examinees display a government-issued ID close to the webcam lens is not an effective authentication measure. Not only are there issues with privacy and ease in the falsification of government-issued IDs, but there are also difficulties in verifying IDs in the best of circumstances—let alone through a webcam lens. Such an authentication method would be easy to circumvent. You can view page 8 of this white paper to learn more
Can you spot any hidden cameras? (There are five!)
Use the arrows to go to the next photo and reveal the answers!
In addition to the security risks associated with proctoring, it is important to note that proctors have a limited number of test-taking malfeasances that they can identify and confront. Let’s take a look at what proctors can’t catch—no matter how vigilant they may be.
Proctors Can't Catch

1. Examinee Pre-Knowledge
Pre-knowledge refers to examinees who have already seen test questions (whether from a braindump site or from previously taking the test) and use that prior knowledge to get a better score on their test. And no matter how vigilant the proctor may be, no human or machine can detect whether an examinee has seen test questions beforehand. You can learn more about pre-knowledge in this article.

2. Proxy Test Taking
In line with our third point about authentication failures above, proctors are unable to catch proxy test taking. Proxy testing is when another person poses as the examinee to take the exam for them. Proctors by themselves have no way of truly knowing whether the test takers they are monitoring are the examinees they say they are, or if they’re hired professionals paid to sit in on the exam. We go into depth about proxy testing in this article, but important to note is that this method of cheating is on the rise.

3. Small Hidden Cameras
Test takers can bring small hidden cameras to their in-person and remote exams to record test content and later sell (to braindumps online or to memorize). Hidden cameras can go on shirts, buttons, contact lenses, eyeglasses, brooches, watches, pens, and more. You can learn more about the dangers of hidden cameras in this white paper.

4. Examinees Who Hack the Test
While less of a widespread issue, examinees can cheat by hacking into the testing server and stealing exam content. (Think Ferris Bueller’s Day Off—when he hacks into the school’s computer system to change his attendance records—but for exams).

5. Test Theft
Examinees can memorize test content to share with others after their exam, hoping either to help colleagues, make money by offering it to others in the course, or be paid by selling it to braindumps.
The above scenarios outline just a few scenarios of cheating and test fraud that proctors cannot adequately detect.
(And if you’re more of a visual learner like me, check out this infographic for the types of cheating and test fraud threats proctors can and can’t identify during an exam.)
In conclusion, we learned that proctoring really isn’t an effective security method just on its own.
(Proctors cannot catch test theft, proxy test taking, pre-knowledge, small hidden cameras, or hacked exams.)
We also learned that understanding how proctors affect the quality of test security efforts during test administration is not as straightforward as it may seem. Some of the security risks associated with proctoring include being able to view the test taker’s screen during the exam; a limited head-and-shoulder-view of the examinee during testing; and authentication failures and privacy concerns.
Up next in Chapter 4, we’ll dive into the effectiveness of proctoring and teach you how to maximize its security benefits.
Then, in Chapters 5-7, we’ll find out whether un-proctored exams can be trusted, the specifics of Record & Review proctoring, and what to consider when choosing your proctoring vendor.
Let’s get going!
The Effectiveness of Proctoring as a Security Measure
In the last two chapters, we went over the benefits and drawbacks of proctoring.
In this chapter, we’re going to show you exactly how effective proctors are at protecting your exam.
We’ll also show you how you can maximize proctoring’s benefits to have the greatest impact on your exam’s security!
Here we go!
How to Measure Effectiveness
Proctoring has been used for centuries, yet our understanding of its actual impact on security is cursory.
Did you know that a proctor’s effectiveness in addressing test security threats varies widely depending on other security factors? You may be surprised to discover where proctors excel and where you may need extra support…
The security solutions that protect tests can be divided into three types:
- Solutions that prevent misconduct
- Solutions that detect and react to misconduct, and
- Solutions that deter misconduct.
(You can learn more about these categories in this guide about the Protection Process.)
Let’s evaluate how proctoring contributes to each of these three categories.
How Effective Is Proctoring?
Deterrence

Effectiveness Level: High
A proctor’s most impactful test security benefit is in their ability to deter test takers from engaging in fraudulent behavior.
Simply by being present, whether it be online or in the room, proctors have a strong effect of convincing test-takers that it is too risky to attempt to cheat. Examinees know they are being watched, and they must modify their behavior accordingly.
This effect is just as strong—perhaps even stronger—when an examinee is taking an online test; they must assume that they are always being watched, and do not have the in-person advantage of waiting for the proctor to turn away or get distracted before attempting cheating.
Regardless of these nuances, it is clear that proctors create a strong deterrent effect.
Detection

Effectiveness Level: Moderate
Proctors are trained to consistently scan the room or testing area in order to discover any infraction of the rules, including the use of cheat-sheets or cell phones, communicating with others, etc.
If proctors discover cheating or harvesting, they are trained (hopefully) to follow a specific protocol to deal with the incident.
In this sense, proctors serve an important detection purpose, and are well suited to uncover certain types of fraud.
However, as we’ve already read, proctors are not equipped to deal with many of the most harmful forms of cheating, such as detecting the use of hidden high-tech devices, catching proxy test takers, or stopping individuals from using pre-knowledge to cheat on an exam. (See Chapter X for more information.)
For this reason, proctors cannot be viewed as a comprehensive solution for detecting all cheating or theft during test administration.
Prevention

Effectiveness Level: Low
From a purely technical view, proctors cannot truly prevent (meaning: stop cheating or theft before it happens) any test security threats while monitoring test-takers.
This means that, regardless of what the proctor is currently doing in the testing room, the test-taker can consult cheat-sheets, look at a neighbor or receive help online, or carry out any other form of cheating at any time—none of which can be prevented by proctoring staff. They might get caught, but they can’t be stopped beforehand by proctors.
Thus, the proctor’s role is a relatively passive one, limited to scanning the room or examination area, looking for misbehavior, and attempting to discourage cheating by just being present.
These limitations make proctors relatively ineffective at directly preventing cheating or theft.
The above analysis is a useful one because it provides us with:
- A fuller picture of how the role of proctoring plays into our exam’s security strategies
- A valuable opportunity to reevaluate how we may be utilizing proctoring
- A start to better understand how we can shore up proctoring’s weaknesses, and
- A way to understand how we can maximize proctoring’s strengths
Let’s zoom in on that last point. How can we truly maximize the benefits of proctoring?
How Can I Maximize the Effectiveness of Proctoring?
Programs that utilize proctors (pretty much all programs!) should start by:
- Examining your current approach to proctoring
- Analyzing the changes you could institute in order to maximize proctoring’s deterrent benefits (this could include increasing the number of your proctors, implementing technology to assist them, improving your proctor training, adding ways to make proctors’ jobs easier, and many others)
- Considering how proctoring fits into your wider test security framework
- Training your proctors continuously to update them on new threats, remind them of their customer service responsibilities, and more. (This could be done through quarterly training videos with short quizzes, intermittent webinars, email updates, etc.)
Since proctoring cannot be viewed as a one-and-done process for security during test administration, each assessment program that utilizes proctors needs to honestly evaluate whether it is relying on proctors as their primary test security tactic.
If proctoring is your primary test security tactic, then this is a great opportunity to institute other security strategies that will not only fill the gaps that proctoring simply cannot address, but also mitigate or lessen any of the risks presented by introducing proctors to a testing room (as discussed in the last chapter).
Let’s check out some of the security measures that help highlight the strengths and overall effectiveness of proctors.

What Security Measures Are There That Can Increase the Effectiveness of Proctoring?
The following security measures can be used in addition to proctors to increase their effectiveness in preventing, deterring, and detecting/reacting to security threats:
1. Conducting Data Forensics
With more sophisticated testing systems, big data approaches, and more complex statistics, real-time data forensics is used to flag candidates for irregular behavior while the test is in progress.
For example, candidate response patterns, timing, and other information can be processed by cloud-based software, enabling the data to be analyzed in real-time. Such analysis could include response similarity, response latencies, and other measures. Some data forensics measures are even built right in to the testing platform!
As a real-world example, Caveon Data Forensics℠ uses latency-based statistics that can alert a proctor that the candidate is proceeding unusually quickly through their examination. The purpose of this forensic measure is to uncover those who could be due to cheating or attempting to steal items. Similarities indices have also been used to flag potential collusion among the candidates or find those who may have pre-knowledge. Such flags, particularly if used in combination with the technologies discussed below, make for a potent combination.
In addition, regular data forensics monitoring should be conducted on a routine basis to detect unlikely test aberrations. For example, running regular psychometric analyses can help you discern whether you have underperforming items and forms and give you an insight into p-values, point-biserial correlations, discrimination values, response latencies, and more.
2. Monitoring the Web
In case anything gets past your proctors’ ever-vigilant efforts, web monitoring for stolen and distributed test content can be an excellent option to shore up your detection measures.
For example, Caveon Web Patrol® efforts have successfully uncovered XX (thousands) of items from proprietary exams that have been exposed online. And since those testing programs know what content is exposed from their exams and where online it has been posted, they’re able to narrow down who may have used that stolen content to artificially pass their exams and understand how much it has already impacted their program.
3. Utilizing Automated Item Generation (AIG)
AIG is another technique that makes one element of the proctor’s job (addressing pre-knowledge) irrelevant.
A large enough item bank utilized properly has many benefits, including making it so that when exam questions are stolen and exposed online, any exposed items are unlikely to be seen by others on the exam. And even if a test taker has memorized test questions and answers, the odds of it appearing on their test are so low that their effort to cheat is ineffective.
A large item pool also means that testing programs can replace items quickly in the event of a breach, limiting the damage from examinees utilizing pre-knowledge, and makes secure test designs (such as CATs, LOFTs, or even a plethora of forms) possible for all programs. Consider using Automated Item Generation (AIG) as an easy and cost-effective way to expand your item pool.
While most AIG methods currently still have the items reviewed by subject matter experts prior to their use on an examination, it is likely that—in the near future—it will be common for items to be generated on the fly. (See: SmartItems)

4. Randomizing Item and Option Order
Randomizing the order of your test questions and answer choices on each administration is a frequently-used way to prevent cheating from taking place on in-person exams or for virtual exams where test takers may gather and take the exam together.
The idea of randomization is that answer keys from static exams will be useless to cheat from on a randomized exam, and looking at the test of another examinee is worthless since their test form is different.

5. Utilizing Secure Item and Test Designs
Test designs such as computerized adaptive tests and linear-on-the-fly testing reduce the overall exposure rate of items, making them difficult to harvest.
Tests with multiple equivalent or equated forms serve a similar security purpose.
Similarly, new types of security-sensitive items are being used that make pre-knowledge irrelevant. The most notable of such new item types is the SmartItem™. The SmartItem renders uniquely, on-the-fly, for every test taker and makes it virtually impossible for test takers to profit by either stealing test content or using stolen content for pre-knowledge.

6. Employing Adaptive Testing
Adaptive testing is another way to present unique content to each test taker.
For example, with Computerized Adaptive Testing (CAT), or Linear on the Fly Testing (LOFT) tests can be administered more quickly, with fewer items, and more securely.

7. Deploying Technology that Detects Hidden Devices
One of the toughest jobs a proctor has is spotting hidden cameras and other devices. Programs spend extensive time training proctors on how to spot these devices.
But there are a variety of technologies that have been developed to detect hidden devices. Options include (but are not limited to):
- Metal-detecting wands: Some organizations have opted to use metal-detecting wands, which detect metal-based devices on the person. However, this can create privacy concerns and is not possible in some countries/regions of the world; further, devices can pass below the sensitive range of such wands.
- Radio Frequency (RF) and Camera Lens Detectors: Radio Frequency (RF) and Camera Lens Detectors are two devices that have not yet been deployed extensively. RF detectors pick up the transmission of radio waves that occur from most devices, while camera lens detectors attempt to pick up the reflection of light from a camera lens. Many devices now have both techniques built in, with amateur versions starting at around $100 and professional versions running into the thousands of dollars. However, a reasonably priced device would provide another critical tool in a proctor’s toolbox. It may also detect currently undetectable devices, including new contact lens-based cameras.

8. Utilizing Artificial Intelligence and Machine Learning
When combined with facial recognition technology and a standard high-definition webcam, AI tech can monitor the movements of candidates to recognize irregularities.
For example, facial recognition can read the positioning of the candidate’s head to identify potential aberrant behavior, so a candidate consistently looking down may be reading off a cheat sheet. Similarly, a candidate may manipulate an object on their person, such as a button camera, to take pictures of the screen. In either case, the behaviors can be trained into the system, and your proctor could be notified.
If proctors are on-site, monitoring may be simply a matter of deploying webcams to test center workstations. The use of such technology might also enable lower proctor-to-candidate ratios, and allow proctors to focus more on providing great service to candidates while reducing the number of test room walkthroughs required.
Of course, these technologies should only be employed when there is absolute confidence they do not introduce bias or privacy concerns.
To learn more about the security solutions that can aid proctors in preventing, deterring, and detecting/reacting to cheating, check out this infographic:
In conclusion, it is shocking how little most exam programs actually know about what proctors really do with regards to test security.
Thankfully, you have a leg up!
Now you know how to best enable your proctors to do their job and be vigilant in detecting cheating threats.
Remember: it is important to closely evaluate just how proctors affect the security of your tests—where proctors improve test security, where they have no impact on test security, and where they make testing less secure. We hope this chapter has been a good guide to help you do just that!
Now that you know how effective proctors are at preventing, deterring, and detecting/reacting to cheating, let’s zoom in even further to understand an important frequently-asked question…
Can un-proctored assessments be trusted?
That’s what we’ll uncover next in Chapter 5.
In the same chapter, we’ll also check out the other security measures that ensure trustworthy test scores on your exams.
Then, in Chapters 6-7, we’ll talk about record and review proctoring and the considerations you should keep in mind when choosing your proctoring vendor.
Forward march!
Can Unproctored Exams Be Trusted?
Now that you’ve got the fundamentals of proctoring down, it’s time to jump into some more advanced material.
Specifically, we’re going to show you whether un-proctored exams can be trusted.
You’ll also learn the security measures that bolster the effectiveness of measurement in certification, licensure, and educational exams.
Can Un-proctored Tests Be Trusted?
This answer might surprise you: Yes—with the right technology and other security measures in place, high-stakes exams administered today can be trusted even without the added component of proctoring.
Are There Scenarios When Un-proctored Exams CAN'T Be Trusted?
Let’s paint this picture with a story:
In 2007, the Boston Globe released an investigative report concerning Army Correspondence Courses.
Senator Edward M. Kennedy, Chairman of the Armed Services Committee, reacted strongly to the report:
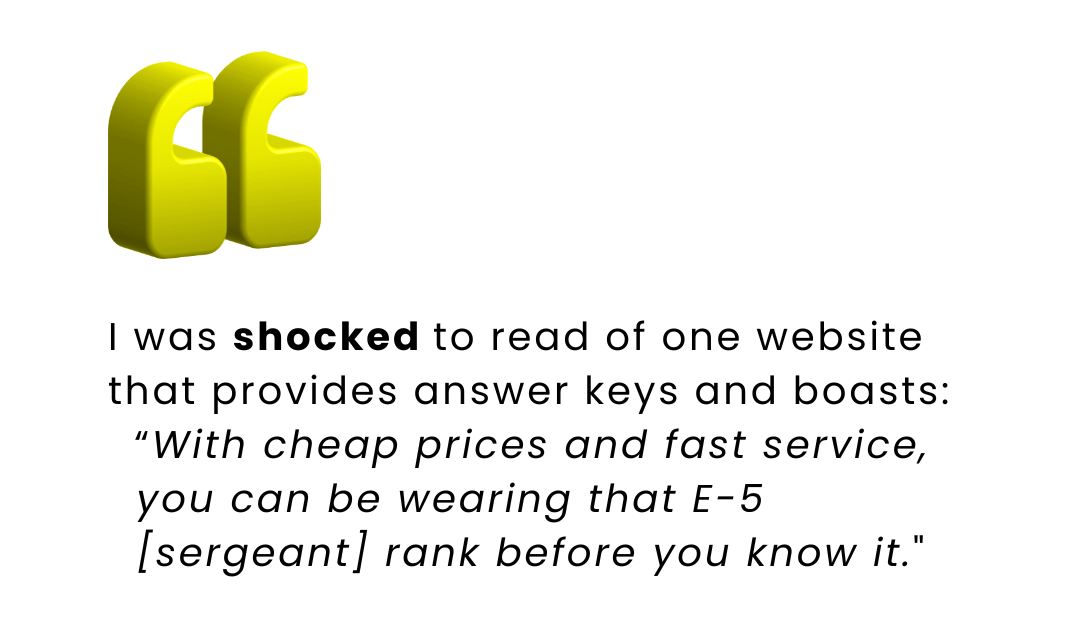
The problem is that many online assessments are essentially un-proctored internet tests that don’t have robust enough security measures in place to prevent, detect, and deter cheating and test theft.
NOTE: Unless online tests can be delivered securely, they should not be used for high-stakes exams.
(By definition, an exam has high stakes if passing or failing the assessment has significant consequences for the test taker. Usually, significant consequences entail opportunities such as getting a job, getting licensed in a profession, getting admitted into a school, getting a diploma, getting a raise or promotion, etc.)
If I don't proctor my exams, what do I need to do to make sure my program's test scores are producing trustworthy results?
There has been interesting progress in the area of secure administrations of un-proctored internet tests. Below are just a few recommendations:
1. Build In “Old-fashioned” Simple Security
In answering this question, we can’t help but be reminded of the old days when taking unproctored tests as a student at university (back then, they were called “take-home” tests). These take-home tests had implicit security built right into them:
- They were really hard. Examinees couldn’t just find the answer to the questions in the university library, online, or in a textbook.
- Examinees might find someone to take the test for them or help them out, but eventually, they would take a few in-class tests (where they couldn’t use a friend).
- The tests were written in the test taker’s own handwriting, which was easily compared with prior copies of their handwritten assignments.
- Later, when he was an instructor at university, Caveon’s CEO, Dave Foster, added another twist to take-home tests: Every student got the same problems, but with different data and different answer options.
Those are just a few of the “build-in” security measures exams from the mid-20th century oftentimes employed.
2. Use Security-enhanced Test and Item Designs
There are many types of secure item and test designs that prevent cheating and theft from the start, before they even have the chance to happen.
Examples of secure test designs include tests that use SmartItem™ technology, CATs, and LOFTs, or even just having a large item bank and a plethora of forms. Examples of secure item designs is the Discrete Option Multiple Choice™ (DOMC) format. All of these reduce the amount of content that each individual examinee can see.
And in addition to decreasing item pool exposure and eliminating many forms of cheating and test theft, these secure test and item designs can also curb ballooning development costs, and more importantly, increase fairness and accessibility.
3. Take Advantage of Biometrics and IP Tracking Capabilities
It is best practice to utilize biometrics to authenticate a test taker’s identity and prevent proxy test taking.
Another security measure many universities have added to their online assessments is the tracking of IP addresses. This enables you to determine whether more than one test is being submitted from the same computer.
4. Utilize Randomization
Algorithms that produce item clones or variants can reduce the ability of test takers to share test content or profit from another’s answers.
Another security measure includes the randomization of answer choices, the random selection of test questions from an item bank, and the prevention of test items from being copied or printed. You can learn more about randomization in this article.
5. Take Advantage of the Proctoring Tools in Your Test Delivery Software
Some test delivery engines (like this one) offer proctor tools that automatically notify you when suspicious events take place during an exam, no proctors needed.
For example, you can receive warnings for examinee behavior such as:
- When “Alt,” “Ctrl,” and “Cmd” keys are pressed. (These are keys often associated with screenshots.)
- When an examinee’s browser is resized. This includes opening browser consoles and inspectors (which can mean another window is viewable that can potentially display answer information).
- When a test taker’s browser is not maximized.
- When the exam is running in the background. This is when a user has changed tabs or applications.
- When there has been a context menu attempt. This detects and prevents right-clicking.
- When an examinee’s mouse has moved outside the browser window.
Automated proctoring tools give room for an unplanned investigation into suspected testing malfeasances. It’s great because the test delivery software gives the test administrator the option of pausing, suspending, or resuming the exam at their discretion.
6. Detect Cheating Using Web Patrol® and Data Forensics™
There are test security strategies available that are far more effective at detecting likely instances of cheating than proctoring. Two of the most effective solutions include monitoring the web for stolen and disclosed test content and routinely running data forensics analyses that detect cheating by looking for unusual patterns in your testing data.
Why? Because conducting forensic reviews of your data and scanning the corners of the internet for stolen content allow you to detect instances of test fraud and uncover vulnerabilities in your testing program that would have otherwise gone unnoticed.
This kind of probing can reveal patterns of answer copying, proxy test taking, large-scale collusion, widespread exam content exposure, and more. (Proctoring does none of those things.)
7. Administer Oral Exams
Remember the day that you took your oral exams? There was no faking. (Unless hiring a proxy to take the test in your place.)
You’re in a room, face-to-face, with one or more professors or exam administrators. (In some cases, with educational exams, these individuals may have taught you in at least one class or preparation course.)
Of course, it is not realistic to administer oral exams for every single individual being certified in a profession or being admitted into the university. But it demonstrates the importance of having several observations which together confirm that the candidate does indeed possess the requisite competence. You can learn more about oral exams in this article.
8. Implement Deterrence Communication Strategies
One of the most powerful things you can do to amplify your security is to communicate its existence. Think of deterrence as a communication plan meant to discourage and inhibit test takers from cheating.
You can get creative with your methods, but deterrence can be as simple as letting examinees know that there are consequences to cheating and test theft.
Deterrence messages should:
- Tell examinees how you detect and prevent fraud
- Show examinees that the likelihood of getting caught is high.
- Establish doubt in the minds of would-be wrongdoers that they’d even benefit from attempting to cheat, let alone get away with it.
Examples of deterrence communications include:
- Requiring examinees to sign an “oath” not to cheat
- Providing test takers with a list of automatic sanctions for cheating before the test starts
- Publicizing the vast array of security methods you are using (such as record & review proctoring, data forensics, web monitoring, etc.)
For even more ideas, you can head to this article to discover ways you can prevent cheating in online exams.
So there you have it!
With the right technology in place, high-stakes exams can be trusted even without proctoring.
Up next in Chapter 6, we’ll zoom in on what record and review proctoring is and how it differs from other forms of proctoring.
Then, in Chapter 7, we’ll look at the considerations you should keep in mind when choosing your proctoring vendor.
Let’s go!
What Is Record & Review Proctoring?
In the last chapter, we learned that un-proctored assessments can be trusted, so long as there are robust enough security measures in place to prevent, deter, and detect/react to cheating and test theft.
But another question that we frequently get asked is:
“How is record and review proctoring different from regular proctoring?”
Good news… That’s what this chapter is all about!
Let’s jump in with some frequently asked questions…
1. What is Record & Review proctoring?
Record and review proctoring (R&R proctoring) is a form of online proctoring, but there are no proctors watching the test taker while the exam is in progress.
Instead, record and review proctoring uses recording equipment to capture the video and audio of the exam administration. The recordings are then reviewed (at a later time) to determine whether cheating occurred, whether exam questions were stolen, and whether the exam was in fact taken securely. Here is a breakdown of some of the key differences:
KEY DIFFERENCES
Live, Online Proctoring
Recorded Test Session Reviews
A form of proctoring wherein a proctor observes one or more test takers live, at the time of test administration.
A form of proctoring wherein a test session is audiovisually recorded and stored for later observation.
Continuous Monitoring
Launched by a Live Proctor
Instantaneous Incident Reporting
More Expensive
Immediate Response to Security Violations
Typically Requires a Third-Party Proctoring Vendor
Ability to Pause or Suspend an Exam
Monitored Later
Launched by an Examinee or Exam Administrator
Delayed Incident Reporting
Less Expensive
Delayed Response to Security Violations
Can Sometimes Be Conducted In-House
No Ability to Pause or Suspend an Exam
Important to note, the “review” portion of record-and-review proctoring could occur a day, a week, or even a year later.
Unfortunately, for many programs with limited resources, often the recordings are never reviewed.
In essence, the main difference between live proctoring and record-and-review proctoring is the ability of the proctor to immediately respond to a security incident.
What happens if a security breach is detected through Record & Review proctoring?
If a security infraction is detected during record and review proctoring (R&R proctoring, the testing program can respond by conducting an investigation, canceling the test score, initiating other sanctions, or by doing nothing at all.
Because of the delayed nature of the review in R&R proctoring, these decisions occur long after the test was taken.
What are the test security benefits of R&R proctoring?
There are security advantages to using record and review proctoring, particularly when compared to using no form of proctoring at all. The benefits include:
- Deterring cheating and theft, and
- Detecting some forms of cheating and test theft
Let’s take a closer look at each one…
DETERRENCE
DETECTION
Basis: With record and review proctoring, a test taker knows that their actions are being monitored and recorded, and that the recording will be reviewed at a later time. This will influence their behavior during the exam.
For some examinees (perhaps most), simply knowing they are being recorded is enough to convince them not to cheat!
Basis: Well-trained and thorough auditors can catch certain instances when test takers violated the security rules. A few examples of types of test fraud that can be caught by reviewers include:
- The use of a prohibited device to look up answers
- The use of a camera to take pictures of test sessions
- Receiving help from someone entering the room, etc.
Caveat: Rather than being deterred, test takers who are determined to cheat will likely adapt to be more covert and creative.
Caveat: Many of the most important types of cheating cannot be seen by reviewing a recording (or even by a live proctor!).
Bonus Points: You can increase the deterrent effect of R&R proctoring by publicizing incidents of cheaters being caught and facing consequences.
This will let examinees know that the security measures are effective, that test security is taken seriously, and that cheating simply isn’t worth the risk.
Bonus Points: Try and review sessions quickly after they are recorded. Catching fraud early enables you to cancel a test score or administer other sanctions.
Be sure to also inform examinees that their scores are provisional until final review, and that releasing official scores might take several weeks.
Just remember that with record and review proctoring, it is always best practice to:
- Clearly communicate to your test takers that scores are provisional until further review
- Review recorded test sessions in a a timely manner.
And keep in mind: if too much time has passed between the test being taken and the recording being reviewed, it will be harder for you to cancel a test score or administer other sanctions if cheating is detected.
What are the security limitations of Record & Review proctoring?
The disadvantages of record and review proctoring include:
- Delayed action
- Reviewing sometimes doesn’t happen
- Compared to other available security options, proctoring is not as effective.
Let’s look deeper into these points.
1. Delayed Action
One major limitation of record and review proctoring is the delay between when the test is taken, when the review is conducted, and when a decision is made to confirm or invalidate the test score.
These delays will mean that the security infractions that are occurring in real time will continue to happen until the review has been completed and the problem confronted.
A ripple effect from this could mean that test content has been unnecessarily exposed, which could facilitate further cheating by other examinees—all without the testing program even knowing it is happening.
For example, a student taking a video of each item on the test will be able to capture the entire test, share it online, and enable more students to cheat, all before the test program has caught anything with their record and review proctoring measures.
Furthermore, a person blatantly cheating by using their phone to look up answers will be able to continue to do so on other tests, and they will likely even receive a high score at the end of those exams as well. That examinee will have already realized the benefits of a higher score (such as a certification, grade promotions, etc.) before the cheating incident is discovered and confronted.
2. Reviewing May Never Happen
Often, the test sessions recorded as part of record and review proctoring are never actually reviewed. This happens because reviewing sessions is a time-consuming and difficult process. Therefore, programs find it easier to simply not conduct any reviews at all! But this is ill advised because it allows cheating and test theft to continue unchecked and with no consequences, thus undermining the validity of test scores.
So say it with me:
Make. Sure. To. Do. The. Review!
3. Proctoring (In General) Is Ineffective
As we’ve discussed in-depth in earlier chapters, proctoring is an ineffective method of test security when conducted by itself. There are many security threats that simply cannot be detected by proctors, no matter how diligent and well trained (e.g., the use of hidden cameras, utilizing test content pre-knowledge, memorizing test content, and others).
Record and review proctoring shares these limitations, and it is often even less effective because the review process is either delayed or it doesn’t occur. (Sad, we know.)
Additionally, record and review proctoring has even greater security weaknesses when the reviewers aren’t trained to reliably detect security infractions.
What can be done to bolster the security of your record-and-review-proctored exams?
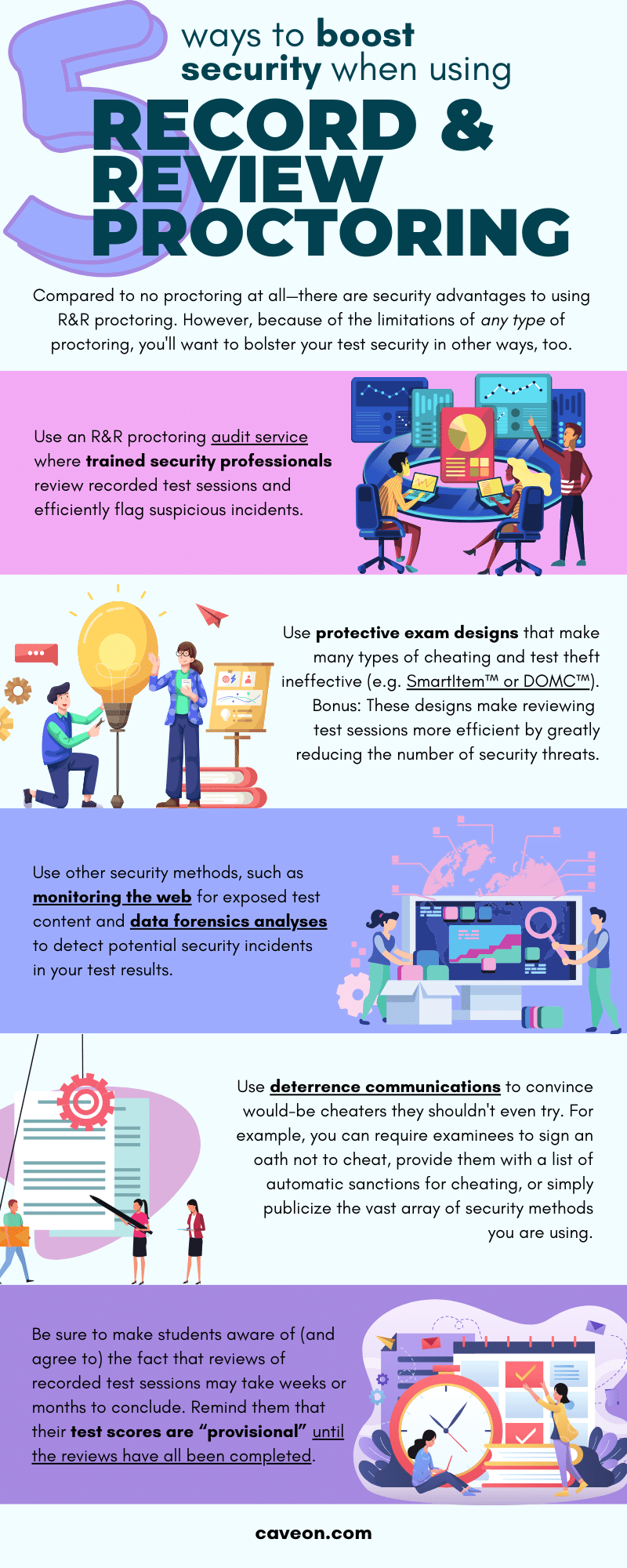
Because of the limitations of record and review proctoring, a program that uses it must bolster its test security in other ways. (You will recognize some of these from the earlier chapter on unproctored exams.) These include:
- Considering the use of a record-and-review proctoring audit service
- Using security-enhanced test and item designs
- Adding an assist to your cheating-detection-measures using web monitoring and data forensics
- Increasing deterrence communications, and
- Making scores provisional until further review
1. Consider Using a Record and Review Proctoring Audit Service
What is an audit?
In a Recorded Test Session Audit, trained security professionals use proven processes and procedures to review video-recorded sessions of online delivered exams.
Audits can be done:
1. As a thorough scrub of all recorded test sessions
- As a random or stratified-selection process, or
- As part of a pinpointed investigation based off of data forensics findings.
How does it help?
Auditors quickly and efficiently screen for obvious signs of test taker misbehavior and other potential incidents, flagging those test administrations for further review. Combing through recorded sessions and following up on potential security incidents helps to ensure the validity of test results.
Additionally, this step allows for trained test security professionals to review your exams for you. Here’s one example of an auditing service that covers all the steps. Security folks are specifically trained to detect cheating and theft, and they know what key behaviors to look out for in test session reviews.
THE BENEFITS OF QUALITY
ASSURANCE AUDITS


DETECTION
Most attempts at test theft and cheating are designed to fly under the radar of traditional security measures. Monitoring—whether remote or in person—is an effective tool for detecting testing irregularities and security vulnerabilities that aren’t visible from an exterior vantage point.
FEEDBACK
Do your test administrators and proctors have all the tools they need to be effective? Do your examinees have proper notice of all the rules and procedures? Gain valuable feedback about the effectiveness of your test administration and security procedures by spot-checking testing sessions.
IMPROVEMENT
After conducting monitoring of your remote test administrations, you’ll have a wealth of data that can help you and your team make actionable test security improvements to your program. Update policies and procedures based on trends and ensure that your security practices remain relevant.
DETERRENCE
Send a message to would-be-fraudsters and test thieves that you take your test security seriously. Monitoring test administrations acts as a strong deterrent for anyone who might intentionally attempt to commit test fraud or steal your test content. It is one more layer of security to strengthen your test program.
2. Use Security-Enhanced Test and Item Designs
What Is Secure Test and Item Design?
Secure exam and item designs make many types of cheating and test theft ineffective. Examples of these types of designs include the SmartItem™, the Discrete Option Multiple Choice™ (DOMC) item, or computerized adaptive tests (CATs). All of these reduce the amount of content that each individual examinee can see.
How Does Secure Item & Test Design Help?
Protective test designs actually have the power to reduce the overall number of test security threats. This, in turn, makes the review process a lot less burdensome.
3. Detect Cheating Using Web Patrol® and Data Forensics
Two of the most effective solutions for detecting cheating include monitoring the web for stolen and disclosed test content and routinely running data forensics analyses that detect cheating by looking for unusual patterns in the testing data.
How Do They Help?
When using any method of proctoring, it’s important to shore up the security weaknesses by probing your test results for patterns and clues that may only be visible in the data (this process is called data forensics).
It’s also best practice to use other security methods, such as actively monitoring the web for incidents of stolen and shared test content.
Why?
Because conducting forensic reviews of your data and scanning the corners of the internet for stolen content allow you to detect instances of test fraud and uncover vulnerabilities in your testing program.
This kind of probing can reveal patterns of answer copying, proxy test taking, large-scale collusion, widespread exam content exposure, and more. (Proctoring does none of those things.)
To make it easier for you, Caveon has a service that does all of it for you:
DATA
FORENSICS

Caveon’s experienced Data Forensics team will analyze your test data using a suite of powerful threat-detecting statistics. These analyses will help you locate threats and eradicate fraud impacting your program.
You’ll learn:
- Whether your content shows evidence of being stolen and used
- If examinees show evidence of using prior knowledge of tests
- Whether security threats appear to increase through the date range of the testing window
REMOTE
MONITORING

Remote monitoring provides a window into your test taker and proctor behavior. First, select whether you’d like Caveon to perform recorded test session audits or remote proctoring quality assurance. Then trained and experienced monitors will evaluate your testing processes.
You’ll learn:
- If your remote proctoring vendors are enforcing policies and procedures
- If test takers display unusual behavior that could signal the need for a deeper investigation
WEB
PATROL

Caveon’s Web Patrol experts provide a high-level analysis of your online threats and vulnerabilities. You’ll receive a letter grade of current online exposure levels and a hierarchical graphic breakdown of potential areas of vulnerability for your intellectual property.
You’ll learn:
- What social media apps or online hotspots have the highest potential for leaked content
- Where you’re at risk for any other types of online exposure
4. Increase Your Deterrence Communications
How Do You Deter Test Fraud?
One of the most powerful things you can do to amplify your security is to communicate its existence.
Think of deterrence as a communication plan meant to discourage and inhibit test takers from cheating.
You can get creative with your methods, but deterrence can be as simple as letting examinees know that there are consequences to cheating and test theft. Learn more about deterrence messages and see examples in this earlier chapter.
How Does It Help?
There are all kinds of different fraudsters out there.
Some can’t and won’t be stopped, especially not by deterrence communications.
But there is an entire subset of opportunistic fraudsters who can be convinced not to cheat! No method of security is a catch-all, so this step is important.
5. Make Scores Provisional Until Further Review
It’s important to set candidate expectations prior to testing.
At the start, candidates should be aware not only of your security policies against cheating and theft, but also of the fact that your test sessions will be recorded and reviewed for violations.
Just as important, make sure test takers are aware and agree to the fact that the reviews of their test sessions will take time to complete (sometimes several weeks or even months), and that their test scores are “provisional” until those checks have been completed.
How Does Setting Expectations Help?
Once a score is official, it is very difficult to rescind it.
Issuing provisional scores gives testing programs the breathing room necessary to conduct a thorough review and any necessary follow-up investigations. This all ensures that official scores are only issued to deserving test takers.
Use this handy infographic for an overview of these 5 additional ways to boost security when using R&R proctoring:
(Click to zoom or view the image in a new tab)
Summary of Record and Review Proctoring
Record and review proctoring has a few important security advantages. It can deter and even detect some forms of cheating and test theft.
However, since since the nature of record and review proctoring includes having a delayed response, and since test sessions are recorded and viewed for security breaches weeks (or sometimes months) later, it is best suited as a backup form of proctoring when other types of proctoring are not possible (e.g., due to budget or time constraints).
Most importantly: as with all proctoring, record and review proctoring is best utilized with other security measures that shore it up (e.g., data forensics, web monitoring, etc.).
So there you have it!
In this chapter, we’ve learned that Record & Review proctoring can play an integral role in any comprehensive security plan.
The basic deterrence and detection benefits of R&R proctoring can be amplified by using a number of additional security methods to provide more comprehensive protection, while common pitfalls of the method can be avoided with proper planning.
Now you know more about automated and R&R proctoring!
Up next, we’ll look at the considerations you should keep in mind when choosing your proctoring vendor.
Let’s go!
What to Consider When Choosing Your Proctoring Vendor
By now you know every testing program is unique. Each has a specific set of needs—from proctoring modalities and user support to additional security layers like AI and security audits.
But there are vitally important software and security features your program should never go without when utilizing proctoring.
In this chapter, we’ll talk about everything you should look for when researching the right proctoring vendor for your program.
Let’s jump in!
Traditional vs. Modern Methods of Proctoring
Traditionally, proctoring didn’t offer much peace of mind.
Nowadays, testing programs should ask for—and expect—great communication, accessible data, and hands-on control.
View the below table for more insight into the strengths and weaknesses of the traditional method of proctoring and the modern, online version of proctoring.
TRADITIONAL METHOD
MODERN, ONLINE METHOD
THE ILLUSION OF CONTROL
You’ll get a report at the end that says “looks good” with little to no third-party accountability or oversight.
ACCESSIBLE DATA & CONTROL
Access data from your multi-vendor solution in close-to-real-time before, during, & after the process.
ACCESS:
ACCESS:
Limited access to data

Vendor as a go-between/middle man

Exam video/proctoring video

Incident logs/exam activity logs
Flagging results/audit results

Response data

System data from end-user computers
TIMING AND RESPONSE:
TIMING AND RESPONSE:

Upon request, long after data is useful

Leads to slow response times and poor security

Near-real time data

Rapid response for better security
Make Sure Your Proctoring Service Offers...
These Software Features:
1. Seamless LMS Integration
A simple, straightforward integration with your LMS should be a requirement for any online proctoring solution.
Gone are the days of spreadsheets and web forms; automation is expected and necessary when transferring exam details.
2. Multi-Modal from One Platform
Are you researching different proctoring styles?
Consider a streamlined approach by selecting a solution that offers a variety of proctoring levels all within a central platform.
3. No Waiting
An online proctoring solution should never get in the way; it should simply support the process of facilitating an exam online.
If your test takers are experiencing delays (and likely agitation), this could impact their performance on the test.
4. A Laser Focus on Learning Validation
What assurance do you have that your test integrity is protected?
Without sufficient security, your reputation may be at risk.
Look for a solution that builds additional security measures into their processes, such as machine learning technology and regular exam audits.
5. Direct, Immediate Support
Test-takers and instructors must have 24-hour access to support in order to ensure a streamlined experience.
As you assess your online proctoring needs, consider your audience in relation to when and where support will be required.
6. Complete Transparency
Curious to see how many test-takers have scheduled their exams?
What violations have occurred to date?
Your solution should offer quick and easy access to all your data, from exam completion rates to violation reports and video files.
These Security Features:
1. Additional Enhancements to Shore Up Security
By now, you know proctoring alone isn’t enough to prevent, deter, and detect/react to security incidents.
Therefore, your proctoring vendor should be able to:
- Work closely with you and provide the necessary data for any additional security measures that will be needed to protect the validity of your exams, OR
- Have quality recommendations for partner-vendors who offer services such as data forensics, web monitoring, and exam audits.
- There are vendors dedicated to ensuring the authenticity of exams and the integrity of organizations. Services like these not only provide added peace of mind throughout the test administration process, but they can guarantee security and reliability.
For example, in the case of data forensics, Caveon uncovers suspicious patterns in your testing data that can uncover threats and expose testing irregularities and other cheating efforts. That data help you learn whether your test takers are colluding or using pre-knowledge, whether proxy test takers are posing as regular examinees, and more.
No matter the route you choose, your test’s security should be thick enough to protect the validity of your exam scores. It should also be robust enough to ensure you won’t have to waste time and money re-writing your exam or responding to needless security breaches that could have otherwise been prevented.
2. Options That Prevent Proctoring Staff from Viewing Test Content on the Screen
Proctors should never be able to view an examinee’s screen or any of the test questions. Why?
Because proctors can be a security vulnerability in and of themselves!
You should always prevent your proctors and test administrators from:
- Seeing the examinee’s screen
- Prompting a test taker toward the correct answer
- Copying down the test questions themselves to sell or distribute to future test takers
And since one of the easiest ways your exam content can end up on the internet is through the unauthorized distribution of test content, every measure must be exhausted to ensure test content is viewed by as few eyes as possible.
Therefore, the proctors themselves should never be able to view the test questions.
3. Enhanced Authentication Measures
As discussed in Chapter 3, it is nearly impossible to discern whether an individual’s ID is real, especially over a webcam.
Below is an ID… Can you tell whether it is real or fake?

That said, there are measures for authenticating test takers. Those include biometric signature analysis and other verification methods that make it far more difficult for would-be proxy test takers to gain access to the exam or falsify a passing score for another examinee.
4. The Option for the Proctor to Pause or Suspend Tests When Signs of Cheating or Test Fraud Occur
This security feature gives room for an unplanned investigation into suspected testing malfeasances.
Less permanent than terminating an exam, the ability for proctors to pause or suspend the test at the first sign of cheating or test fraud provides proctoring staff the opportunity to take a deeper look into a situation. This prevents the need to move forward with more permanent measures, such as invalidating a score.
5. Easy Access for Your Testing Staff to View Recordings for Quality Assurance Audits
In an ideal world, proctors will always be well-trained and highly invested in every test session they monitor.
But that isn’t always the case.
Proctors are not always well-trained, they are not infallible, and like all humans, they can be easy to fool (see how easy it can be to use hidden cameras during a proctored exam in this video).
For example, perhaps your data forensics measures uncovered a potential cheating ring and you need to take a closer look into the individual test sessions of examinees, or perhaps you discovered a cache of live exam questions on the internet and need to find out how widely they were spread.
Whatever the scenario, access to recorded test sessions is a high-priority checklist item to ensure that test takers—and test monitors—are following the rules.
You should expect each of these features from your online proctoring solution. When implemented, your assessment program will have the resources needed to detect, deter, and prevent test fraud.
To learn more about the standards for online proctoring, please view this white paper:
Conclusion
We hope you’ve enjoyed our Ultimate Guide to Proctoring in 2023!
Now we’d like to hear from you:
- What proctoring measures has your testing program utilized?
Is it live, in person proctoring or online proctoring? Record and review proctoring or automated proctoring? Whatever it is, we’d love to hear from you.
More Proctoring Insights
Want to learn more about all things proctoring?
Check out these additional resources!

Test Security Standards for Online Proctoring
Learn the objective and practical standards for securely administering tests using online proctors. While there are many additional practical and procedural concerns regarding online proctoring, Caveon’s standards focus solely on those related to test security.

Test Fraud Threats
There are 14 exam security threats that could undermine your test’s security. What are they? (Hint: they are divided into two categories, cheating and theft.)

Quality Assurance for Exams
Are your proctors doing a good job? Caveon’s Data Forensics℠, Monitoring, and Web Patrol® services are teaming up to deliver a multi-perspective view of your exam program’s health and security.

Record & Review Proctoring: Downloadable Guide
The information contained in this downloadable guide is also included in Chapter 6.

How Examinees Use Hidden Cameras to Steal Exam Content
This white paper discusses the power, affordability, and accessibility of modern hidden cameras. It showcases how easy it is to use hidden devices, even (and almost especially) when a proctor is present, and talks about ways to make it more difficult for these methods to work.

The Past, Present, and Future of Proctoring
When it comes to test security, it is only by looking at the history of proctoring and the ways it has—and most importantly has not—evolved in the current era that we can truly understand the role that proctors should play in protecting the validity of our tests now and in the future.
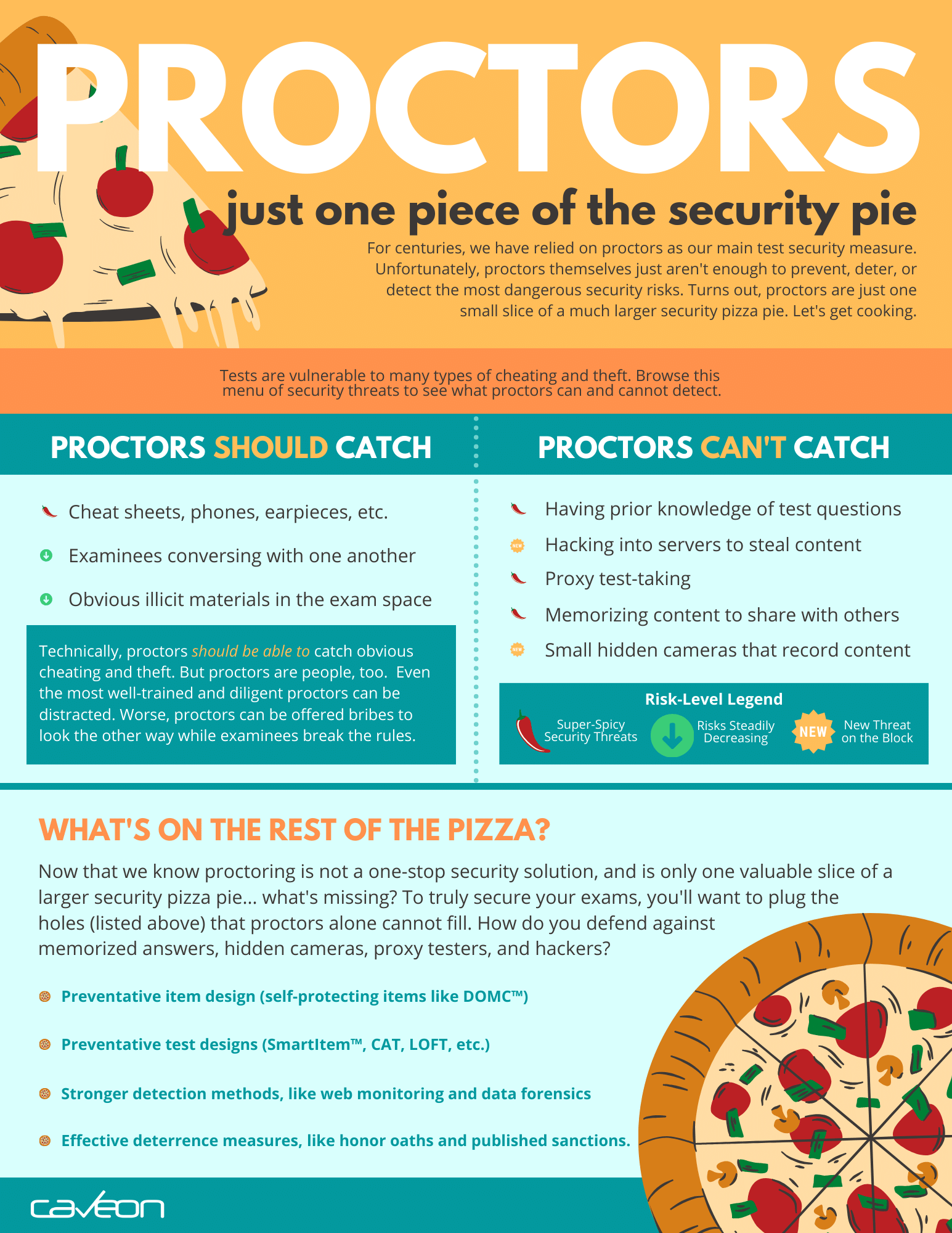
Proctors: One Piece of the Security Pie
Tests are vulnerable to many types of cheating and theft. Browse this
menu of security threats to see what proctors can and cannot detect.
5 Ways to Boost Record & Review Proctoring
There are lots of security advantages to using R&R proctoring. However, because of the limitations of any type of proctoring, you’ll want to bolster your test security in these other ways.

Are Proctors Enough?
We are big proponents of online testing, but only if it is secure online testing. Relying on proctors as the only security measure isn’t enough. Here is a more robust approach.

The SmartItem™:
An Ultimate Guide
The SmartItem is a revolutionary concept in item and test design. It can prevent all test theft and almost all forms of cheating.
In this in-depth guide, we’ll teach you what a SmartItem is, how it works, its many benefits, and lots more. You’ll also find multiple case studies and get to play with a real-life SmartItem!
Curious What Strategies Can Enhance Your Proctored exams?
Tell us a little about your organization and unlock a new era of security today!














